Qubole Service Offering QDS Health Cloud On Amazon Web Services (AWS)
HIPAA (Health Insurance Portability and Accountability Act of 1996) is a United States Federal legislation that provides data privacy and security provisions for safeguarding medical and patient health information (herein referred to as “PHI”). In 2013, the HIPAA Omnibus Rule was put in place by the Department of Health and Human Services to implement modifications to HIPAA in accordance with the guidelines set forth in 2009 by the Health Information Technology for Economic and Clinical Health (HITECH) Act concerning the responsibilities of business associates of covered entities.
Qubole working with our partners has evaluated these requirements and implemented separate data services specifically for customers who are interested in solving big data challenges who also happen to be designated as Covered Entities or Business Associates as defined by the various Health Insurance legislation.
The following guidelines are mandated for both our customer’s protection and also for the privacy and security provisions mandated by the Department of Health and Human Services.
- Only environments defined at https://www.qubole.com/about-qubole/trust/hipaa-compliant/ are considered eligible for protection under HIPAA, HITECH, or the Omnibus Rule. NO OTHER Qubole Environments are eligible for these protections and customers are not permitted to process PHI-related workloads and jobs in other environments. Customers doing so would be in violation of the Qubole terms of service and the business associates agreement.
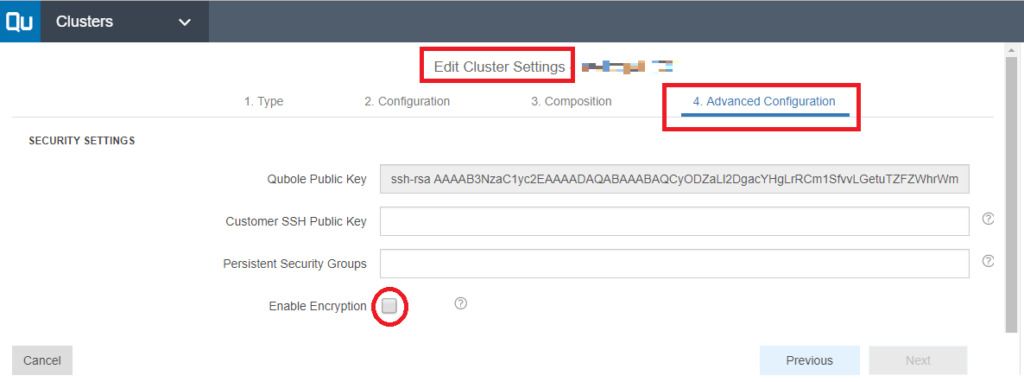
- Qubole feels that it is prudent to use encryption, therefore, Qubole has enabled encryption on clusters within your account and at the completion of all workloads, your data will be written securely by default. You can find this setting within your clusters as shown below under advanced configuration.
- Customers must only use AWS IAM Roles for access to their AWS Cloud accounts, details describing the recommended permission set for these IAM roles can be found below.
Policy Objects
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"ec2:AuthorizeSecurityGroupEgress",
"ec2:AuthorizeSecurityGroupIngress",
"ec2:AttachVolume",
"ec2:CancelSpotInstanceRequests",
"ec2:CreateSecurityGroup",
"ec2:CreateTags",
"ec2:CreateVolume",
"ec2:DeleteSecurityGroup",
"ec2:DeleteTags",
"ec2:DeleteVolumes",
"ec2:Describe*",
"ec2:DescribeVolume",
"ec2:DetachVolume",
"ec2:ImportKeyPair",
"ec2:ModifyInstanceAttribute",
"ec2:RequestSpotInstances",
"ec2:RunInstances",
"ec2:StartInstances",
"ec2:StopInstances",
"ec2:TerminateInstances"
],
"Resource": [
"*"
]
},
{
"Effect": "Allow",
"Action": [
"sts:DecodeAuthorizationMessage"
],
"Resource": [
"*"
]
}
]
}
{
"Version": "2012-10-17",
"Statement":
{
"Effect": "Allow",
"Action": [
"s3:GetObject",
"s3:GetObjectAcl"
],
"Resource": [
"arn:aws:s3:::your-unique-resource-location-goes-here/*"
]
},
{
"Effect": "Allow",
"Action": [
"s3:GetBucketAcl",
"s3:GetBucketLocation",
"s3:ListBucket"
],
"Resource": [
"arn:aws:s3:::your-unique-resource-location-goes-here"
]
}
]
}
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "iam:GetInstanceProfile",
"Resource": "arn:aws:iam::your-aws-account-number:instance-profile/your-optional-vpc-name"
},
{
"Effect": "Allow",
"Action": "iam:PassRole",
"Resource": "arn:aws:iam::your-aws-account-number:role/your-optional-vpc-name"
}
]
}
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"s3:DeleteObject",
"s3:GetObject",
"s3:GetObjectAcl",
"s3:PutObject",
"s3:PutObjectAcl"
],
"Resource": [
"arn:aws:s3:::your-unique-resource-location-goes-here/default-location/*", "arn:aws:s3:::your-unique-resource-location-goes-here/default-location*"
]
},
{
"Effect": "Allow",
"Action": [
"s3:GetBucketAcl",
"s3:GetBucketLocation",
"s3:ListBucket"
],
"Resource": [
"arn:aws:s3:::your-unique-resource-location-goes-here"
]
}
]
}- Customers must configure a separate AWS Virtual Private Connection (VPC) or a separately dedicated subnet for PHI workloads and data that will be processed. An example of the VPC configuration can be found in the following document which also describes the basics of subnetting: https://docs.aws.amazon.com/AmazonVPC/latest/UserGuide/VPC_Scenario2.html#VPC_Scenario2_Implementation
- Customers must work with a Qubole Solutions Architect or Customer Success Manager to ensure that configurations are optimally and properly configured.
- Customer and Qubole must mutually agree to a Business Associates Agreement (BAA). Qubole services are designed to leverage customer and cloud services and controls and the BAA must specify these responsibilities thereby requiring mutual agreement to these controls.
- Customers must define and populate specific Qubole roles for Customer users (Employees and Users) to ensure that the principles of least privilege have been followed for Customer users who are accessing Qubole.
Customers must only deploy Qubole with a custom Hive Metastore which would be dedicated to the Customer. Your Qubole Solutions Architect or Customer Success Specialist will be able to help you set this up in your account.


